
Welcome
Welcome to week 4 of NUSTART. This week you will learn all about security at UKNNL and how you can contribute to keeping us safe and secure. Before getting started, watch this short video from Des Wright, Chief Nuclear Officer and Senior Information Risk Officer, talk about the importance of security to UKNNL.
Security teams at UKNNL
In your first week, you completed the General Security Awareness e-learning module where you learned about how your own actions help protect our assets and keep our business secure.
While we all have a personal responsibility when it comes to security, we also have different teams and specialist roles that are dedicated to keeping us safe, secure, and compliant with both legal and regulatory requirements. Collaboration with these teams is crucial to maintaining our strong security culture, so this week you will be introduced to our different security teams and learn who to contact for advice on any aspect of security.
Security and Resilience
Our Security and Resilience (S&R) Team is responsible for the security of all our people, facilities, and physical assets. They make sure we are compliant with all the regulations governing nuclear and maintain operational security providing advice and guidance to the business. Our Personnel Security team, or vetting team, sit within the S&R function. The vetting team check the identity and integrity of everyone working for or on behalf of UKNNL.
You will learn more about the roles within S&R and how you may interact with the team over the next few steps.
Security Liaison Officer
The Security Liaison Officer (SLO) is the local security representative at each of our facilities. They provide a local point of contact for security and ensure that all our security requirements are cascaded throughout the business.
Your SLO will be able to advise you on your facility’s security arrangements and how to protect UKNNL assets at your location. They will make you aware of any specific security measures that you need to be aware of at certain times, for example when building work is being carried out at your site.
SLOs also monitor and report on compliance with UKNNL security standards and will often carry out spot checks to ensure that the appropriate security procedures are being followed.
Your SLO is your local contact for security advice.
You can find full details about the Security Liaison Officer role on Q-Pulse in IMS-01-SLO v3.
SLO activities
Security reviews
All employees are subject to security reviews. For those colleagues holding Baseline Personnel Security Standard (BPSS), assurance checks are undertaken annually by your line manager. Managers receive an automated Business World alert asking for confirmation that there are no security concerns. National Security Vetting clearances are reviewed in line with ONR regulations. For colleagues holding Security Clearance (SC) the review period is every 10 years and for employees holding Developed Vetting (DV) clearance the review period is seven years.
Colleagues holding DV or SC will also be subject to an annual security appraisal which involves completing a Security Appraisal Form with their team manager.
It’s important you engage in this process and are proactive in arranging a security appraisal. Failure to do so could result in the withdrawal of your security clearance and the removal of access to facilities and/or network.
Change in circumstances
Vetting aftercare maintains your security clearance throughout your employment at UKNNL. Any information that might constitute a security concern that could affect your suitability to hold or continue to hold security clearance must be reported to your line manager. In some instances, your line manager may need to share this information with the vetting team.
This could include:
- Criminal offences - you are arrested, refused bail, received a police caution, reprimand or final warning or are convicted of an offence (other than minor road traffic offences)
- Significant physical or psychological problems, such as depression or emotional instability
- Addiction, for example, gambling, alcohol or drugs
- Serious security breaches
You should also inform security vetting of any changes in personal circumstances.
These could be:
- Changes in your financial circumstances, which may include:
- a significant change in finances that makes a real difference to your financial situation, either by making it more difficult or by improving it, for example, incurring more debt than you can easily manage, bankruptcy or receiving a lump sum for example by inheritance or as a gift.
- A planned reduction in income or savings e.g maternity/paternity leave for an extended period; reduction in working hours or a partner retires.
- A planned increase in income or savings e.g paying a mortgage off, removal of financial liability such as a loan, expected investment maturity, expected inheritance, UKNNL promotion, significant bonus payment.
- change of Nationality - you acquire a new nationality or renounce a nationality that you previously held
- a marriage or civil partnership or you start living with a partner as a couple.
- when a new co-resident starts living with you in shared accommodation (Developed Vetting (DV) only).
All reports will be treated confidentially but may be shared on a need-to-know basis.
In some circumstances, information may need to be shared with the HR team, Sellafield site security (if you are based at Sellafield and the Office for Nuclear Regulation (ONR). The vetting team will work with you and relevant partners to mitigate any potential risk to our organisation.
We recognise that you may feel nervous about reporting a change in circumstances to the vetting team but it’s important to remember that their primary aim is to mitigate risk rather than remove your clearance. You can reach the security vetting team at nnl.security.vetting@uknnl.com. For urgent matters click the Report an incident button on the nucleus home page.
Security for Line Managers
Line managers have additional responsibilities when it comes to security. As they oversee teams, they’re often the first to notice if someone might be struggling or at risk of being exploited. If you're a line manager you must complete NN5825 Security for Line Managers e-learning to help you recognise and address these risks effectively, ensuring a safe and secure environment for everyone.
For everyone else, don’t worry—you can move on to the next step.
Pass management
While it’s normal for many organisations to ask their employees to carry or wear an ID pass, due to the nature of our work, we place strict controls on when and where you should wear your pass.
Please familiarise yourself with the following rules and be prepared to respectfully challenge if you see someone wearing or using their pass incorrectly:
- passes must always be worn and displayed within UKNNL premises - the only exception is where there is an agreed overriding safety requirement.
- passes are not to be displayed outside UKNNL premises (except whilst on a nuclear licensed site where UKNNL is located).
- pass holders must not allow anyone else to use their pass.
- lost passes must be reported immediately to the local Security Liaison Officer (SLO), and the loss recorded on the UKNNL online reporting system, OSHENs.
- ensure you comply with local and company access control requirements
- passes that are worn, damaged or where the photograph is no longer a good likeness of the holder must be replaced.
- if you have a name change, for example due to marriage, you must request an updated pass.
- passes must be treated responsibly and held securely. - it is your responsibility to look after your pass.
- passes should be held in official passholders with lanyards or other appropriate authorised holders to minimise loss/damage.
- passes must not be left in vehicles.
- only one UKNNL security pass may be held by an individual.
- passes must be handed in if you are going to be absent from work for an extended period, for example maternity or paternity leave, career break, long term sickness or as a result of suspension.
- passes must not be tampered with, be given to another person to use and the security access control system must not be abused.
Travelling abroad
Working in the UK nuclear industry may make you of interest to foreign intelligence services when travelling abroad – regardless of whether you have access to sensitive or protectively marked material.
In some instances when you are travelling abroad, whether for business or pleasure, you must notify UKNNL Security vetting.
The IMS document Reporting Requirements for Overseas Travel (IMS-I-070) provides information about the countries that you need to notify the UKNNL Security vetting about, and how to register your travel on Business World. Please find and read the policy on Q-Pulse and make sure you know what to do to travel safely abroad.
If you have a need to take UKNNL IT kit or information abroad, you must follow the export controls procedure. You'll learn more about this in step 17.
Chief Information Security Officer function
What do the CISO Function do?
Everything we do at UKNNL is informed by information, from developing advanced reactors, to supporting university-led projects, to managing monthly payslips.
The expertise and insight held within all types of UKNNL information is vast, and sometimes highly sensitive. This makes it valuable.
Unfortunately, others may wish to exploit this value - from hostile states looking to shortcut their nuclear programmes, to cyber criminals looking to ransom our information for money.
Occasionally, mistakes can also put UKNNL information at risk.
The UKNNL Chief Information Security Officer (CISO) function's role is to help UKNNL protect its information. The CISO team provide specialist advice and support to help everyone across UKNNL protect our information. They do this as part of day-to-day business, and also as part of responses to specific incidents.
What can the CISO function help you with?
As well as working closely with IT to help monitor and ensure UKNNL information is secure, the CISO function provides a range of other services. Examples of when you may need to reach out include:
- if you are starting a new project or procurement and want to ensure it has the right level of security included from the start.
- if you are travelling overseas on business and need to use UKNNL kit securely.
- if you need advice on sharing information securely with organisations outside UKNNL.
- if you have urgent/immediate concerns that UKNNL information is being put at risk
How to contact CISO
You can contact the CISO function for non-urgent queries about projects, procurements and travel etc, at nnl.ciso.team@uknnl.com
Don't forget that a range of supporting instructions and procedures are available on Q-Pulse. UKNNL's CISO Function page also provides useful information about how we all have a role to play protecting our information.
CISO activities
Information security and data protection
Data protection is ensuring fair and correct use of information about people – people like you, your colleagues, friends, and family. The Data Protection Act 2018 (DPA) and General Data Protection Regulation (GDPR) provide rules on how data must be handled and processed to ensure it is used fairly, lawfully, and transparently.
Every day, we all handle personal data in our roles – we just may not realise it.
Understanding what this data looks like and the handling principles is vital. Mistakes can be serious and could result in UKNNL facing regulatory interventions and fines. More importantly, we could also risk causing harm to those who trust us with their information.
If you have a serious or urgent concern regarding data protection contact the IT Service Desk in the first instance on 01925 933777 who will advise on next steps.
Learn more about GDPR and data protection by completing NN5803 Data Protection Essentials e-learning. If your role means you’ll be processing personal data or controlling data (e.g. Human Resources or payroll) you may need to complete NN0417 General Data Protection Regulation Advanced. Speak to your line manager if you are unsure.

Social media
Many of us have a presence on social media, whether it’s Facebook, LinkedIn or TikTok. Whilst seemingly harmless, it’s important to remember that these sites allow individuals to obtain personal information about us.
For example, creating an account often requires us to handover personal information such as our name, date of birth, address and/or phone number. Savvy criminals will often collect data from many different sources, building a picture of where you live, places you visit, clubs or communities you join and information about your family. You may need to consider discussing with your close friends and family what impact their actions may have on you and UKNNL when using social media, for example, if they share your role, what you do and where you work.
As an employee of UKNNL you are one of our most valued assets, but this also makes you a potential target for those who might wish to do us harm. Please ensure that your social media presence never brings UKNNL into disrepute . Never disclose your security clearance level online.
Learn how to stay safe on social media by visiting Q-Pulse and reading IMS-GN-EUG: Online Social Networking – End User Guidance

Personal devices
Mobile devices can be taken on site, some areas may restrict you from having a mobile on your person and you should follow any local signage, or instructions given at the time. You can use your phone during working hours providing it is appropriate and not a disruption to you, your work or your colleagues. You are not permitted to take photographs on any UKNNL premises unless authorised by a Security Liaison Officer.
All your UKNNL work should be carried out on UKNNL IT and devices. Personal laptops, desktops and IT devices do not have the same stringent security standards as UKNNL devices and are at greater risk of being compromised. Transferring data between UKNNL and personal devices is strictly prohibited due to the risk of breaching GDPR regulations. If the kit you have been provided with isn’t right for what you need, always contact the IT service desk who will help you find a solution.
Don't forget, when working from home, smart speakers (such as Amazon Echo/Alexa) may also pick up sensitive conversations; make you sure you turn them off or move them away from where you work.

Reporting security incidents
If you need to report a security incident, you can do so quickly and easy through the ‘Report an incident’ button on Nucleus home page. There are three reporting routes for information, physical and personnel security issues, events or concerns. You can also find a reporting route for environment, health, safety & quality.
Visit the reporting incidents page now to learn what steps to take should an incident occur and make a note of any phone numbers you might need.
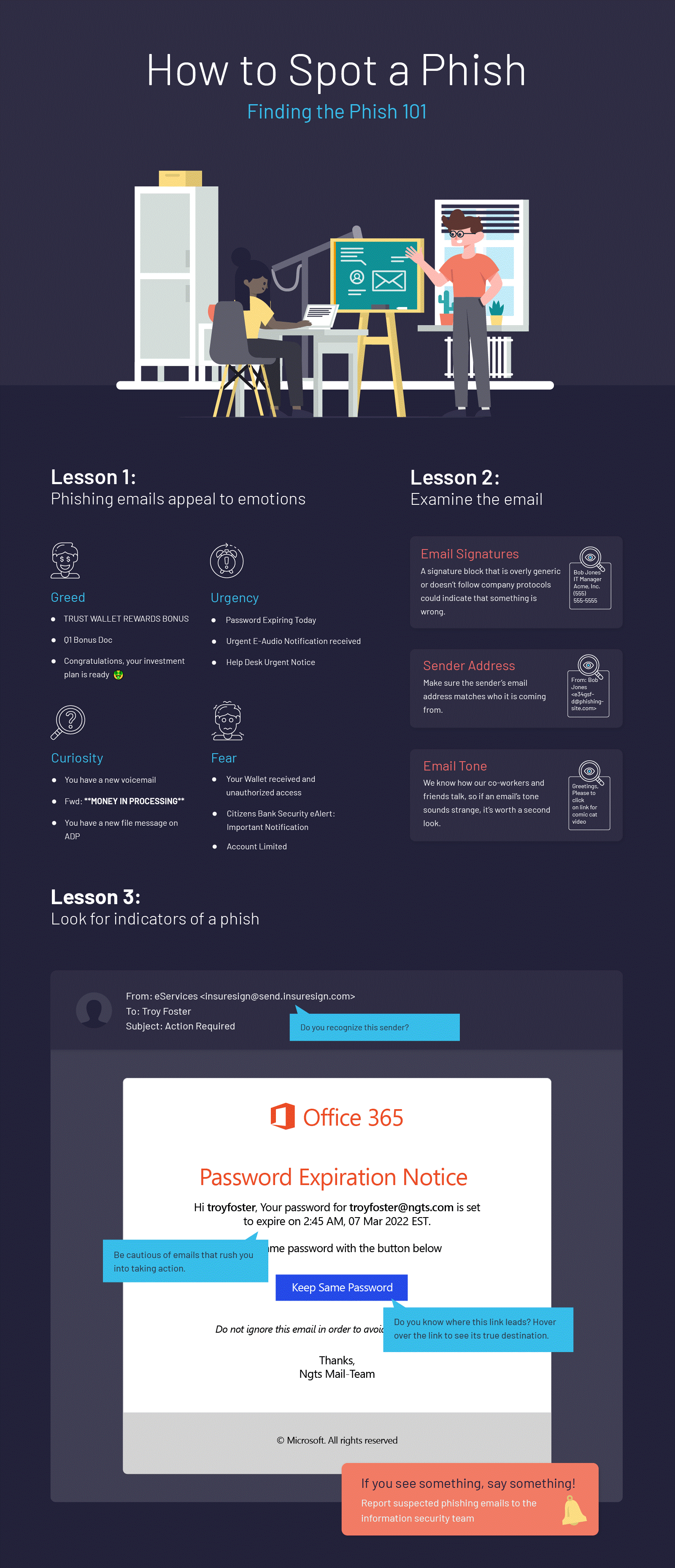
Phishing
Phishing is how criminals try to introduce malicious code onto our network by sending emails containing malicious links or attachments. Attackers may also try to manipulate you into sharing sensitive information, such as usernames, passwords, email addresses and credit card details; as well as coerce you into making fraudulent payments. Phishing doesn't only happen through email; phone calls or voice phishing are increasingly common, along with SMS and other 'messenger' types of phishing. Everyone is at risk of falling victim to a phishing attack and it's up to all of us to remain vigilant. In all cases, don't interact, click or supply any details if you feel it isn't appropriate to do so. You can report suspicious emails using the 'Report Phishing' button on the top right of the Outlook menu bar. For anything else, use the report an incident button on Nucleus home page.
Information – export controls
The information which UKNNL holds and processes could be subject to export controls. An “export” occurs when information, including information sent electronically or communicated verbally, crosses the UK border. An intention to export is not relevant. An export therefore includes the taking or sending of any information outside of the UK via the following means of transmission:
- physical exports, for example laptop, mobile device, memory stick, disk or hard copy document.
- electronic transfer, for example email, fax, video conference, intranets or shared data environments.
- remote access from overseas to emails or corporate networks, for example, technology contained on an individual’s laptop will be exported if that individual takes the laptop outside the UK.
UKNNL’s policy is that laptops should not be taken out of the UK without approval from IT (export control, CISO and S&R). If permission is granted, advice must be sought from the Export Control Administrator to ensure that no information is inadvertently exported and that any information which is to be exported is under the relevant licence.
Further information on export controls is given in IMS-P-243.
Glossary
Security & Resilience (S&R)
The Security & Resilience team are responsible for all our people, facilities and assets.
Personnel Security
The Personnel Security team (sometimes referred to as the Vetting team) check the identity and integrity of everyone working for or on behalf of UKNNL.
Security Liaison Officer
Security Liaison Officer’s (SLO’s) are based at each of our facilities and act as a local point of contact for security, ensuring security requirements are cascaded throughout the business.
Information Management System
The information management system is similar to an electronic library, and it is the way we manage interrelated parts of our business to achieve our objectives. You might hear the phrase ‘check the management system’ 'look on IMS' or 'Check Q-Pulse' these are all used interchangeably and refer to checking what information is recorded under our IMS arrangements.
Q-Pulse
Q-Pulse is the is the electronic system or tool that provides a home for all of our information management arrangements.
OSHENS
Our event reporting system, pronounced OH-SHENS. To ‘raise an OSHENS’ is to log an event on the system.
Assets
Our assets include nuclear material, proprietary technology and information, our people, facilities, business processes, government classified information and our IT network.
Vetting
The method used to check the identity and integrity of an individual working for or on behalf of UKNNL.
Security Check
Security Check or SC clearance is required for posts involving regular and uncontrolled access to SECRET information and/or occasional, supervised access to TOP SECRET information assets.
Developed Vetting
Developed Vetting or DV clearance is used for positions that require substantial unsupervised access to TOP SECRET information and assets.
Vetting Aftercare
Aftercare is the management of personnel security. Its purpose is to investigate and monitor any continuing or arising security concerns and minimise risk.
Office of Nuclear Regulation
The Office of Nuclear Regulation (ONR) is the UK’s independent nuclear regulator with the legal authority to regulate nuclear safety, civil nuclear security and safeguards and conventional health and safety at nuclear licensed sites in the UK.
Chief Information Security Officer
The Chief Information Security Officer (CISO) function's role is to help UKNNL protect its information. The CISO team provide specialist advice and support to protect our information.
Hostile States
A term used to describe a foreign state that may carry out hostile activity such as sabotage, espionage and foreign interference.
UK General Data Protection Regulation
Sets out the responsibilities of organisations and individuals when processing personal data in the UK.
Data Protection Act 2018
The Data Protection Act 2018 (DPA) sets out the framework for data protection in the UK. It sits alongside and supplements the UK GDPR.
Personal Devices
Any portable technology such as mobile phones, tablets, laptops and USB flash drives.
Incidents
An event that may compromise information, physical or personnel security e.g. sensitive information shared in error, a person unwilling to show a pass etc.
Phishing
A technique used to try and deceive people into revealing sensitive information such as usernames or passwords through fraudulent emails or websites.
Export Controls
Controls placed on the export – the sharing of information - either electronically or verbally, across a UK border.
Baseline Personnel Security Standard (BPSS)
The standard level of screening used in the energy sector for positions working with or for Government Departments.
End of week checklist and further activities
To continue your progress, consider these questions:
- Watch a webinar hosted by David Cowan from the Nuclear Decommissioning Authority talk about a ransomware attack on Copeland Borough Council in 2017 to learn about what really happens during an attack, the response and the road to recovery. Visit the Copeland Webinar
- Visit Get safe online a useful site that can help you stay secure at home.
- Visit the Behavioural Based Observations & 24/7 report library (under UKNNL Applications > Corrective Action Management) and view some of the sustainability observations (filter by topic of conversation) and consider submitting some of your own.

.png)